US-Mexico connectivity push drives autonomous freight corridor project
Concern about tariffs hitting flows between the US and Mexico is not slowing a push ...
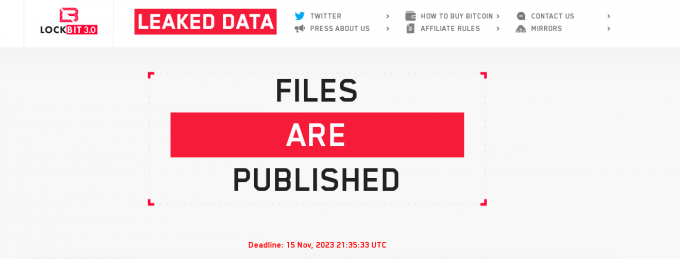
A ransomeware cyber-attack on a UK trucking company has again brought home the very real threat companies face in an increasingly digital world.
Welsh firm Owens Group was the victim of a cyber-attack this month, resulting in its internal data being published on Lockbit’s website ...

Comment on this article